Fortify with Firewalls
Build a digital fortress with our firewall protection, guarding your network against all intruders.
Smart Security - IPS/IDS
Our Intrusion Prevention and Detection Systems offer intelligent threat detection and rapid response to keep your data safe.
Dynamic Web Filtering
Experience worry-free web browsing with our advanced proxy services that dynamically filter content in real-time.
E-mail Fortification
Trust our email protection to shield your inbox from spam, malware, and phishing threats for secure communications.
Antivirus Armor
We provide powerful antivirus solutions to shield your devices, ensuring airtight protection against viruses and malware.
Data Lockdown with DLP
Keep your sensitive information under tight wraps using our Data Loss Prevention measures, ensuring confidentiality and compliance.
Organizational Excellence
Elevate security with strong organizational measures and periodic authorization reviews, creating a protective shield around your data.
Penetration Tests for Unbreakable Defense
Our regular penetration tests are your secret weapon to bolster defenses, leaving no chink in your digital armor.
Cybersecurity Technological Aspects
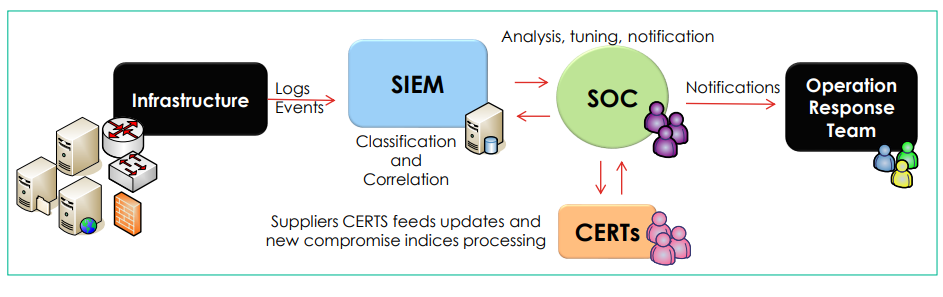
SOC - Security Operation Center A managed service composed of a team of cybersecurity experts, combined with the use of a SIEM (Security Information and Event Management) and the CERTs (Computer Emergency Response Teams) of solution providers, enables the detection and notification of cybersecurity threats by correlating logs and events from the components that make up the infrastructure.
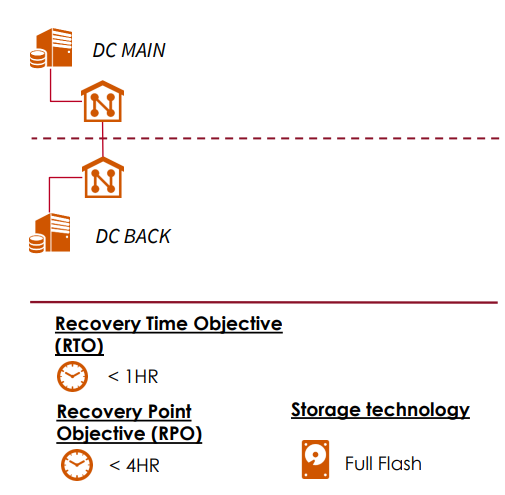
Disaster Recovery & Business Continuity
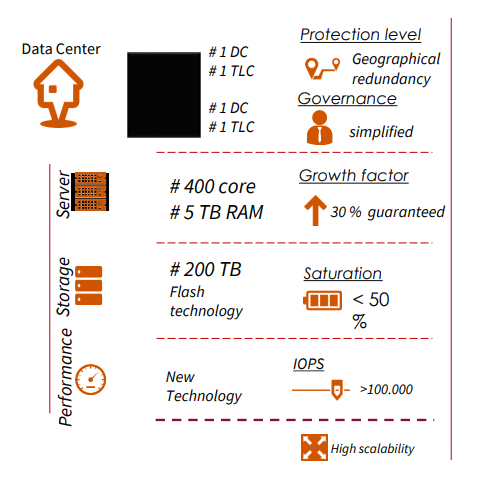
The infrastructure includes the separation of the Data Center and the TLC Room to simplify operational management. The two sites are located in separate locations to ensure geographic protection.Each Data Center is capable of independently providing all services. The structure is sized to meet the most stringent RTO (Recovery Time Objective) and RPO (Recovery Point Objective) requirements.
Vulnerability Scanning
Deploy an advanced automated scanning solution that identifies and reports potential security weaknesses in your ICT systems, ensuring threat assessment and timely remediation.
Penetration Testing
After vulnerabilities are discovered, our team initiates comprehensive testing to assess and report potential exploitation techniques for each weak point, equipping you with actionable insights for strategies.
Web Application Testing
Majority of cyber-attacks use flaws in the web applications used by organizations such as on-line forms, blogs, forums, incorrect coding, misconfigured web servers, queries and many other things.
Social Engineering Testing
This test is designed to verify employee adherence to the security policies and best practices defined by management for correct data disposal and incident reporting.
Assessment Report
We carry out a thorough assessment with reports that identify vulnerabilities and provide recommendations and best practices to be implemented to eliminate or mitigate the cyber risks.
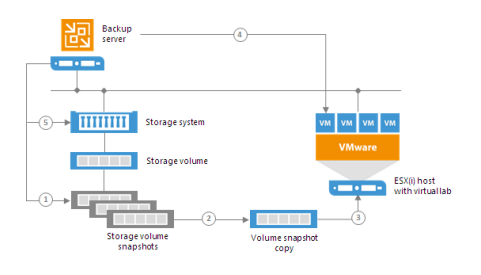
Backup Sytem
- Data deduplication
- Item level recovery
- Native tape support
- Run one or more VMs directly from a backup in an isolated environment and have the ability to troubleshoot, test and train on a working copy of the production environment, without impacting business operations
- Use storage snapshots to quickly create complete isolated copies of your production environment for fast and easy testing and troubleshooting
Network Structure
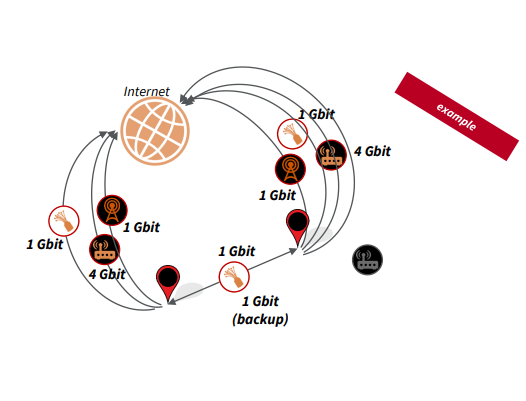
- Redundant and heterogeneous Internet (WAN) connections at both sites (Radio/Copper/Fiber)
- Ownership of telecommunications equipment
- Over 500 IPv4 addresses owned
Connectivity
- 4 Core Switches
- 1 External Perimeter HA UTM Firewall
- 1 Internal Perimeter Firewall
- 1 Firewall for Link Segregation
LAN
Contact Us
Get In Touch
Address and Mail
Address
Galattic Cyberspace Ltd 2023,
Dubai International Financial Center
PO BOX 12513 Dubai, UAE Suite 1500
The risk associated with an event is calculated based on the combination of two factors: 1. Impact 2. Probability of occurrence.
About Us
We are Galattic CyberSpace, We Create Build Develop Solutions
for Cable OR Wireless Network Infrastructure
Creating Cable and Wireless Network Infrastructures
Simplified management, including for complex companies and infrastructures. This is the main strength of the active devices that we use in the realisation of cable or wireless network infrastructures.
Network access control
With our network infrastructure solutions, it is possible to add a feature to switches that allows for the control of physical access to the local network and automatically assign the proper membership area based on the type of user who is connecting.
Disaster Recovery & Business Continuity
The infrastructure includes the separation of the Data Center and the TLC Room to simplify operational management.